It’s that time of the year again. The period around password day always sees a spate of near identical articles. You know the sort: “Did you know 123456 is the most used password?” and “New technology means the end of passwords”. Enough already.
Why are we still using passwords?
Passwords date back as far back as ancient Rome and we’ve been using them to limit access to computers since the early 1960s. Back then, computers were bigger than many starter homes and were shared. Passwords were a simple way to segregate information and users.
For an in-depth run down of the history of passwords, check out this great blog.
Why, nearly 50 years later, do we still rely on passwords so much?
We know that they are very vulnerable to brute force attacks—Google “password cracker” to see just how easy it is to find an application that will cycle through millions of common variants.
They are also prone to social engineering. Not the Hollywood-style portrayal of a guy in a hoodie using some incredible divination skills or guessing them character by character, social engineering is a sophisticated and very effective technique.
Sadly, many of the actions that have been taken to improve passwords, like enforcing length/complexity rules, have introduced new problems. In reality, the benefits are often small compared to the inconvenience caused—they make it far more difficult for humans to remember their passwords, and more likely to reuse the same ones or write them down.
86% of security decision makers said they’d do away with passwords if they could. Does that mean that 1 in 7 are fans?
IDG survey of security decision makers, April 2019
We’re suffering from a serious case of inertia when it comes to passwords. If we can’t find a suitable alternative, we should at least be trying to fix the way we use passwords. Too many people are still making obvious mistakes.
ji32k7au4a83 looks like a great password, find out why it isn’t.
The Verge, May 2019
Busting some password myths
Chances are if you’re reading our blog you’re already pretty clued up on cybersecurity. So rather than repeating things you already know, we thought that we’d tackle some of the biggest myths surrounding passwords.
- 8 characters is a good length. Nope. The length of your password isn’t really any indication of how strong it will be. You just need to look at this article on different websites’ criteria to know that length restrictions don’t have much merit.
- You should change your passwords regularly. Rubbish. You only need to change your password if you think it may have been compromised. If you’ve taken the right steps in the first place to create a secure password, changing regularly is only going to cause more hassle for you—it’s unlikely to have any significant impact on your likelihood of being breached.
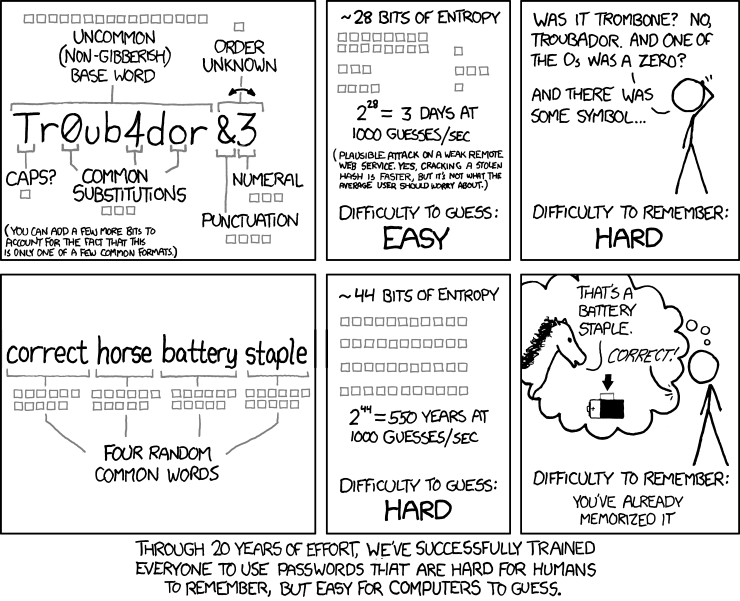
- There’s a great trick to create easy-to-remember passwords. Newsflash… hackers use the same internet as the rest of us. There are a number of tricks, like replacing letters with numbers/punctuation (for example “p4$$w()rd”). But if you’ve read about it, hackers probably have too. And they will have adapted their techniques to get around them.
Couple of caveats to that last one. Some techniques—like using the first letters of the words to a favourite song or poem—are probably fine for protecting low-risk things like newsletter subscriptions, just avoid big hits and go for something more obscure. And combining three or more random words can be quite effective, especially when combined with some random capitalisation. This can generate passwords that are relatively easy to remember while being relatively hard to crack.
But wait you say, isn’t two-factor authentication the answer? In short, no. It’s a fantastic step forward, but it’s no panacea. And not all implementations of 2FA are secure. A couple of years ago, NIST changed its advice on using 2FA to say that using codes sent by SMS were no longer considered secure.
Look out for Part 2 covering what you can do to use passwords better and a look at what’s on the horizon.
Posted by John on 15 May 2019